Are you certain your Linux servers in your data center are free from vulnerabilities? If not, you need to scan them immediately. Jack Wallen shows you how with Nessus.

Image: Mark Agnor/ Shutterstock
Nessus is one of those tools every network, system and security admin should have at the ready. Once up and running, you can easily set up scans to check your data center servers to make sure everything is on the up and up. And knowing whether or not your systems suffer from vulnerabilities is one of the more challenging aspects of your job.
Fortunately, Nessus scans are incredibly easy to run. They do take some time to complete, but the process of launching a scan should take you no time.
You do have to have Nessus installed and working. I’ve covered that process in How to install the Nessus vulnerability scanner on Rocky Linux. So make sure you follow that howto, so you have an instance of Nessus ready to go.
Let’s get to scanning.
SEE: Kubernetes: A cheat sheet (free PDF) (TechRepublic)
How to set up a scan in Nessus
Log into your instance of Nessus. We’re going to first run a basic network scan. Click New Scan in the top right corner of the window. In the resulting screen (Figure A), select Basic Network Scan.
Figure A
” data-credit>
You have a few scan options with the Nessus Essentials package.
In the next window (Figure B), you need to first give the scan a name (which can be any human-readable name) and a target (either an IP address or FQDN).
Figure B
” data-credit>
Setting up a basic scan with Nessus.
Since this is a basic scan, you won’t need to set up credentials, so just click Save and your scan is ready to run.
How to run the new scan in Nessus
You should find yourself on the saved scan list. Click the run button (right-pointing arrow) associated with the scan you just created (Figure C).
Figure C
” data-credit>
Our scan is saved and is ready to run.
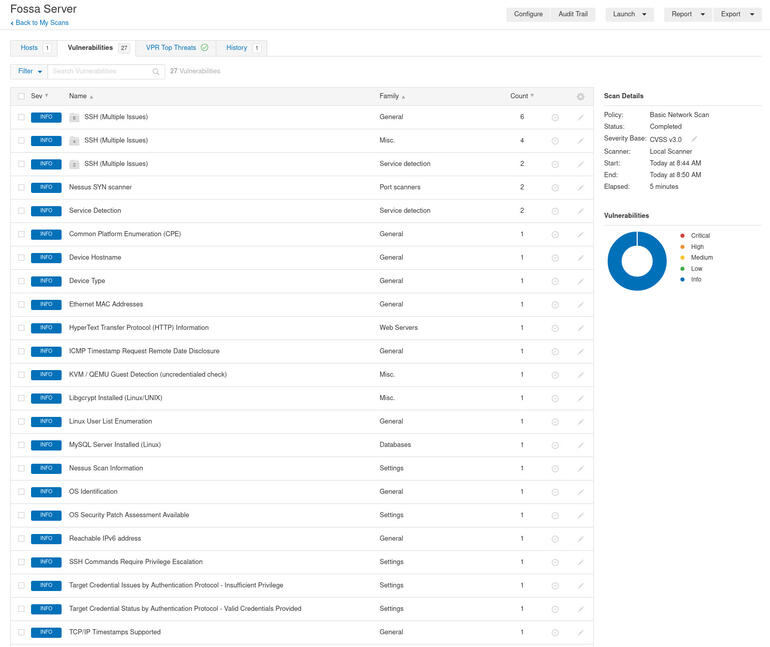
Launch the scan and either sit back and wait for the results or take off to another task. The basic scan should take anywhere from 5-20 minutes to complete. Once it finishes, you can click on it to view all of the vulnerabilities it has discovered (Figure D).
Figure D
” data-credit>
Our basic scan has plenty to report on Ubuntu Server 20.04.
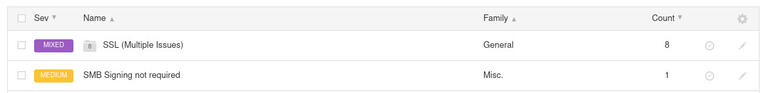
After running the scan on an updated Ubuntu Server 20.04, Nessus came back to report zero vulnerabilities of concern. However, running Nessus on my Pop!_OS 21.04 desktop came back with a slightly different story (Figure E).
Figure E
” data-credit>
Nessus found vulnerabilities in both SSL and SMB.
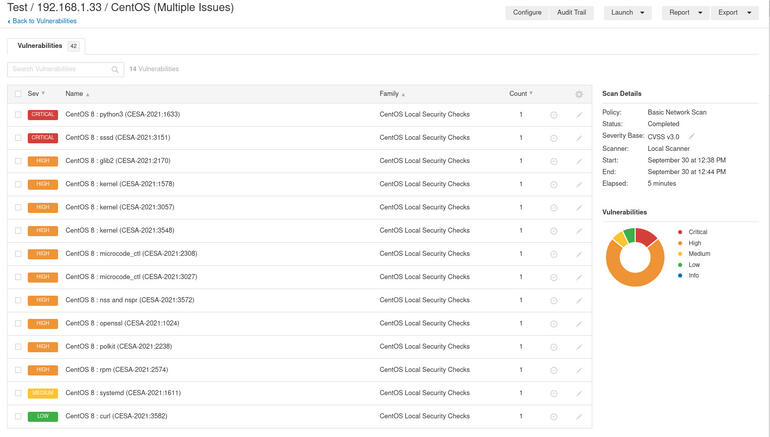
A scan of Rocky Linux came back with a pair of critical vulnerabilities and several high vulnerabilities (Figure F).
Figure F
” data-credit>
Rocky Linux had several issues that should be immediately addressed.
If you see a label marked Mixed, make sure to click on it so it will display all of the different vulnerabilities associated with that particular package. And should Nessus discover any vulnerabilities, make sure to address them immediately, otherwise your data center servers are at risk. If you do run an upgrade on the server hosting Nessus, you might lose connection to the scanning platform. Should that occur, you’ll need to restart the Nessus daemon with the command:
sudo systemctl restart nessusd
And that’s all there is to running a basic vulnerability scan with Nessus. Next time around we’ll dive into some more complicated scans. Until then, keep checking those data center servers for vulnerabilities. Make this a habit, otherwise, those vulnerabilities can creep in and leave your systems wide open for attack.
Also see
Source of Article