The Cisco Talos report exposes new malware used by the group to target Internet backbone infrastructure and healthcare organizations in the U.K. and the U.S.

Two reports from cybersecurity company Cisco Talos provide intelligence about a new attack campaign from the North Korean threat actor Lazarus. The reports expose new malware and tools used by the group, which keeps using the same infrastructure.
Jump to:
What is this new malware attack chain?
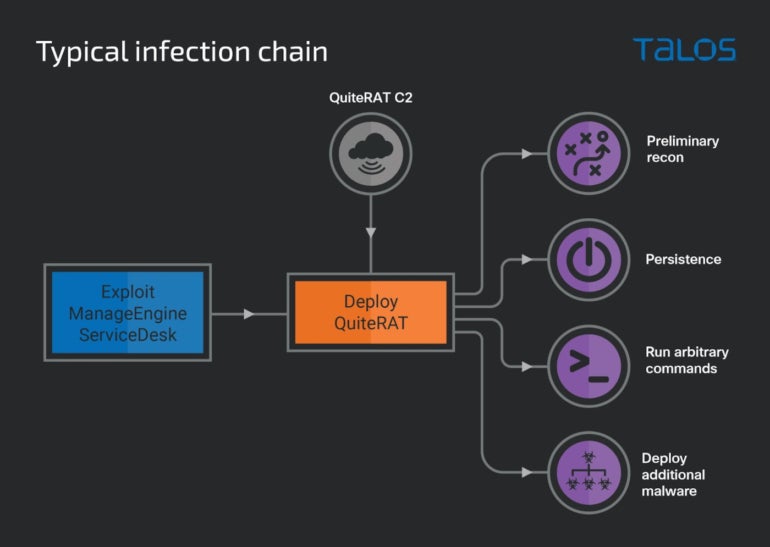
The researchers observed the Lazarus group successfully compromise an internet backbone infrastructure provider in the U.K. in early 2023, deploying a new malware dubbed QuiteRAT.
The initial compromise was done via exploitation of the CVE-2022-47966 vulnerability, which affects Zoho’s ManageEngine ServiceDesk. The threat actor leveraged an exploit for it five days after the proof of concept was publicly disclosed. The successful exploit downloaded and executed the QuiteRAT malware, hosted on an IP address used by Lazarus since at least May 2022.
Once the malware has been executed, it starts sending initial information about the system to its command-and-control server and waits for an answer, which might be a direct command to the malware or a Microsoft Windows command line to be executed via the cmd.exe process. The initial information is being encrypted and sent to the C2; it consists of network configuration information (i.e., IP address and MAC address) and the currently logged in user name (Figure A).
Figure A
The Lazarus group’s new arsenal of malware
Lazarus has used various malware in this attack campaign: QuiteRAT, CollectionRAT, DeimosC2 and malicious Plink.
QuiteRAT
QuiteRAT is a remote access tool mostly built using Qt libraries and developer code. The use of Qt for writing malware is rare because this framework is usually used to develop graphical user interfaces. Qt use makes the code more complex to analyze for reverse engineers, and might render machine learning and heuristic detections by security solutions less reliable because they might not flag the use of the Qt libraries as malicious.
It is not the first time Lazarus has used the Qt framework for developing malware. MagicRAT malware was already using it, and similarities between both (e.g., having the same abilities, the same encoding scheme and similar functionality to allow them to remain dormant) indicate that QuiteRAT has been derived from MagicRAT. Additionally, Cisco Talos notes that the last MagicRAT version they observed was compiled in April 2022, while the QuiteRAT samples they found were compiled in May and July 2022. This might indicate a switch from MagicRAT to QuiteRAT, which is smaller and more compact: MagicRAT takes 18MB, while QuiteRAT is around 4MB to 5MB.
CollectionRAT
CollectionRAT is another RAT used and probably developed by Lazarus. The malware is a packed Microsoft Foundation Class library-based Windows binary that decrypts and executes the actual malware code on the fly. The malware gathers information from the system it infected and provides different usual functions for a RAT: it allows data collection, can provide a reverse shell to run arbitrary commands on the system, read and write on the disk, and download and execute additional payloads.
The researchers found information that might indicate CollectionRAT has spawned from another malware family known as EarlyRAT, which is attributed to the Andariel subgroup of Lazarus. One CollectionRAT sample used the exact same code-signing certificate as an older version of EarlyRAT from 2021.
DeimosC2
DeimosC2 is an open-source post-exploitation C2 tool that leverages multiple communication methods in order to control machines that have been compromised. It is used by Lazarus as a means of initial and persistent access.
The researchers found a Linux DeimosC2 implant on the infrastructure, indicating the threat actor planned to deploy it during the initial access to compromised Linux-based servers. The implant was not heavily customized, which might be an indication that Lazarus is still in the process of testing it or getting used to it.
The implants typically have various RAT capabilities, such as executing commands, stealing credentials, downloading and executing more payloads.
Malicious Plink
Plink, also known as PuTTY Link, is a legitimate open-source tool used by network administrators to get reverse tunneling capability when needed. Lazarus used the tool as-is in the past, but the group has started to modify the source code of it to embed the reverse tunnel command strings in the binary itself.
Lazarus keeps reusing the same infrastructure
Although the group makes a lot of changes to its arsenal, the North Korean state-sponsored Lazarus threat actor “continues to use much of the same infrastructure despite those components being well-documented by security researchers over the years,” according to Cisco Talos. This is good news for security because it allows IT staff and researchers to track the threat actor more easily and protect against it. Yet it might also mean that Lazarus is confident enough in their operations and don’t think it’s necessary to change much of their attack infrastructure.
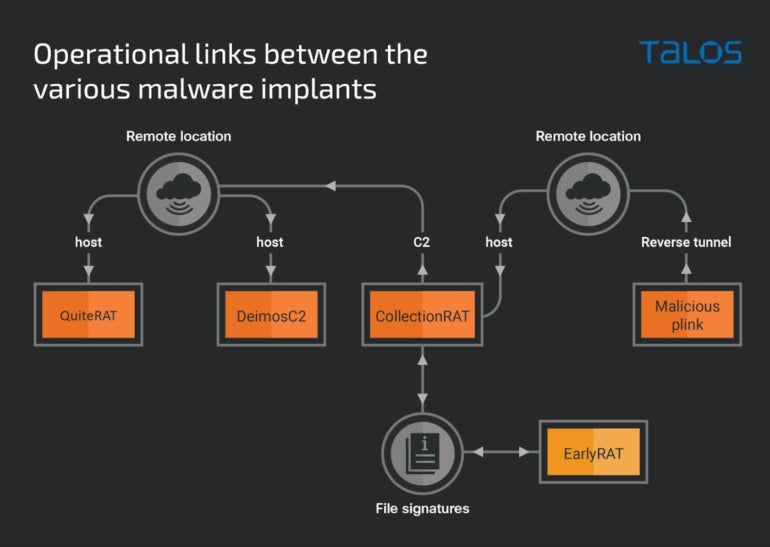
QuiteRAT has been found in the same remote location as DeimosC2 agents and MagicRAT malware used in 2022 by Lazarus. The location has also been used for CollectionRAT.
The different tools and malware used by Lazarus can all be tied together using the infrastructure (Figure B).
Figure B
How to protect your business from this security threat
In this attack campaign, the initial compromise was done by exploiting a vulnerability affecting Zoho’s ManageEngine ServiceDesk that was patched around November 2022. Tips for protecting from this security threat include:
- Keep software and operating systems up to date and patched.
- Monitor networks with security solutions.
- Make rules to detect the communications from the malware exposed in this attack campaign.
- Monitor IP addresses used by the threat actor.
- Deploy security solutions on endpoints and servers in order to detect malware and tools that might be used to attack your organization. These solutions should also monitor the email contents, attached files and possible links to malicious content.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.
Source of Article