Kali Linux has been a fan-favorite for penetration testing for a long time, and with a refresh and new tools, the latest iteration is better than ever.

For anyone who deals with security, penetration testing is often a necessary evil. Sometimes you cannot know what vulnerabilities lie in your systems until you intentionally try to break them. Fortunately, with the help of penetration testing, you’re not actually breaking those systems, you’re only knocking on their doors to see how possible it is to crash through.
SEE: Password breach: Why pop culture and passwords don‘t mix (free PDF) (TechRepublic)
That’s why platforms like Kali Linux are so important. With pen-testing Linux distributions, you have all the tools you need to run nearly every known penetration test on your servers, desktops and network.
Offensive Security recently unleashed the first iteration of Kali Linux for 2022. In this new release, dubbed simply 2022.1, you’ll find improved accessibility features, SSH compatibility for legacy protocols and more new tests to try.
Let’s dig into Kali Linux 2022.1 and see if this Linux distribution should be your go-to penetration testing tool.
What’s new in Kali Linux?
As with every release of a distribution, the first thing people want to know is what’s shiny and new? Kali Linux 2022.1 has plenty of newness to keep it feeling fresh and modern.
First, the developers added a few visual refreshes by way of new wallpapers for the desktop, login and GRUB display. The desktop is Xfce (Figure A) and the developers have done an outstanding job of keeping it clean and minimal.
Figure A
I’m glad the developers opted to keep the desktop clear. So often, developers with such a distribution throw everything at the desktop (such as Konky) to give the user all the information they may or may not need at a glance. This can easily wind up being too distracting and cluttered to be useful, especially when using a distribution as a virtual machine, where desktop real estate is precious.
Speaking of virtual machines …
The installation route I chose was a virtual appliance (which can be downloaded from the Kali Linux site). Unless you need to install Kali Linux on bare metal, I highly recommend going this route as it’s much more efficient to install and use. Instead of booting the OS when you need it, you can start the VM and have it land in the exact same state as when it was last used. To make the virtual route even more appealing, when running on VirtualBox, you can resize the VM window out of the box (as you can with Ubuntu Desktop). Also, the shared clipboard is enabled by default, so copying and pasting between host and guest (and vice versa) works as expected.
One thing to know about going the virtual machine route is the default credentials are kali/kali. You should make sure to add a new user with:
sudo adduser USERNAME
Where USERNAME is the new username. After that, make sure to add the new user to sudo with:
sudo usermod -aG sudo USERNAME
Where USERNAME is the new username.
Speaking of the terminal …
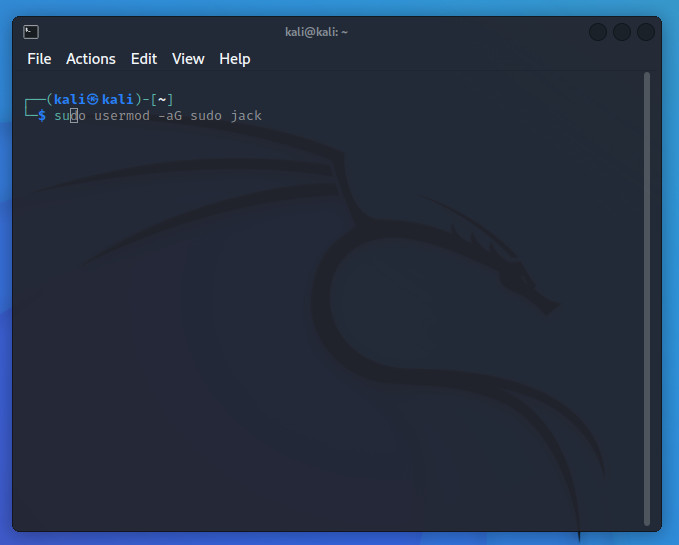
One thing I really appreciate about what the developers have done is tweak the terminal window so it autocompletes commands. This could come in very handy with a distribution that could see you working within the terminal window more than when on other desktops. For example, I start typing sudo and the terminal autocompletes with the last sudo command I entered (Figure B).
Figure B
SSH backward compatibility
The developers of SSH are always evolving the software, protocols and encryption algorithms. It’s not uncommon that an encryption algorithm will be found to include vulnerabilities. When that happens, the SSH developers might disable it (to protect users). Given the nature of Kali Linux, it’s important to be able to continue testing for those vulnerabilities, so the developers have made it such that the SSH client can be configured for wider compatibility (so it can communicate to as many SSH servers as possible).
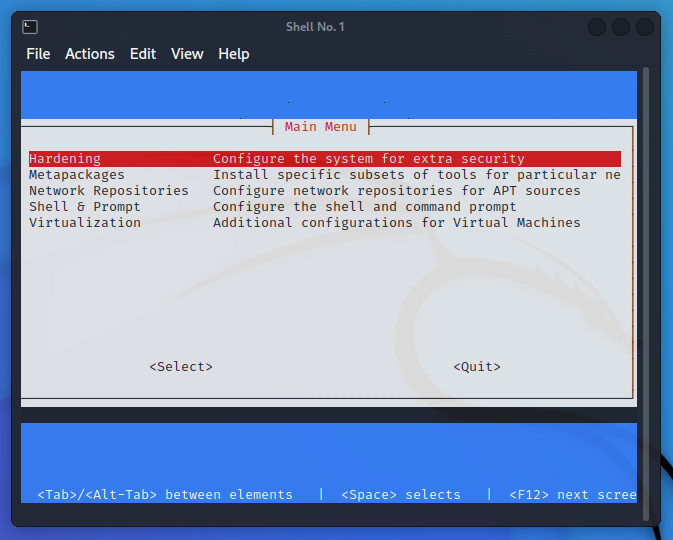
When using SSH in wide compatibility mode, legacy key exchange algorithms (such as (diffie-hellman-*-sha1) and ciphers (such as CBC) are enabled. In order to enable wide compatibility mode, you must go to Desktop Menu | Settings | Kali Tweak. In the Kali Tweak tool (Figure C), select Hardening.
Figure C
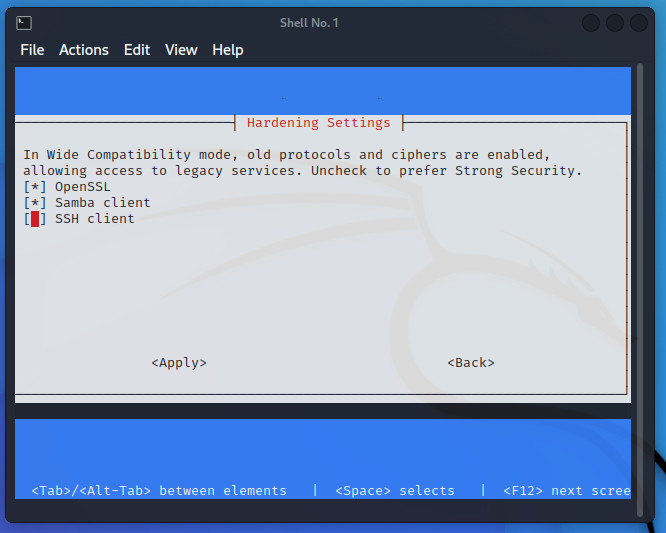
In the resulting window (Figure D), use your cursor keys to select SSH. Hit the space bar to select, tab down to Apply, and hit Enter on your keyboard.
Figure D
New tools for even more tests
Kali Linux 2022.1 adds six new tools to further expand your testing efforts. Those tools are:
- dnsx—run multiple DNS queries.
- email2phonenumber—OSINT tool that allows a user to locate a phone number via an email (NOTE: I’ve yet to actually find this tool on Kali Linux and although it says it can be installed with the command sudo apt install email2phonenumber, I’ve found no such success).
- naabu—a fast port scanner.
- nuclei—template-based, targeted scanning.
- PoshC2—a proxy-aware C2 framework that uses post-exploitation and lateral movement.
- proxify—a proxy tool for HTTP/HTTPS traffic capture, manipulation and replay.
Along with the new tools, you’ll find Kali Linux contains all the usual suspects for your penetration testing needs. Combined with the new tools, the visual refresh and the wide compatibility mode, Kali Linux 2022.1 might be the best release of this OS yet. Download either the virtual appliance or an ISO to install on bare metal and find out if this latest iteration will be your go-to pen test platform of choice.
Subscribe to TechRepublic’s How To Make Tech Work on YouTube for all the latest tech advice for business pros from Jack Wallen.
Source of Article



