Published on: April 22, 2024
Cybersecurity firm Cisco Talos warned on April 16 that cybercrime groups have been targeting VPN (virtual private network), SSH (secure socket shell), and web app services with global, brute-force cyberattacks since March. The attacks have disrupted several service providers with account knockouts and denial of service, according to cybersecurity researchers at Cisco Talos.
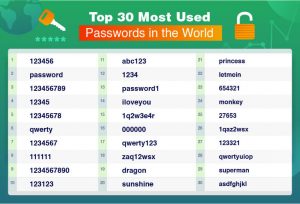
The undisclosed threat actors have been using 4,000 IP addresses to conduct trial-and-error and password-spraying strategies in an attempt to access company and customer accounts. An estimated 2,000 usernames and passwords have already been compromised at services like Fortinet VPN, Checkpoint VPN, and SonicWall VPN, Cisco Talos reported.
“These attacks all appear to be originating from TOR exit nodes and a range of other anonymizing tunnels and proxies,” Cisco Talos added.
Other source vectors include Proxy Rack, VPN Gate, Nexus Proxy, and IPIDEA Proxy, which make the origin points of the attacks untraceable.
The cybersecurity firm recommended that all services in the VPN, SSH, and web services sector block the 4,000 IP addresses and affected usernames and passwords to limit their networks’ vulnerability.
To improve medium-term security, Cisco Talos said all web services should patch network vulnerabilities as soon as possible. Botnets are increasingly using cheap, large-scale attacks to find unauthorized access points to organization networks.
“Users should be vigilant against DDoS botnets and promptly apply patches to safeguard their network environments from infection, preventing them from becoming bots for malicious threat actors,” Cisco said in its advisory.
In 2023, a new kind of botnet malware called “Condi” exploited a security flaw in certain kinds of TP-Link Archer Wi-Fi routers to take over the routers and use them to conduct large-scale distributed denial-of-service (DDos) attacks. The security flaw has since been patched.
However, the developer of Condi is selling the malware’s source code as a service on its Telegram channel, promising that its botnet attacks will continue.
Source of Article