Tom has covered numerous cybersecurity topics whilst working as a writer. Based in the United Kingdom, Tom enjoys cooking and going on country walks in his free time.
Thousands of healthcare organizations have been targeted by cybersecurity threats in the last few years, with hospitals accounting for 30% of all large-scale data security incidents. In this article, we’ll be assessing the state of healthcare cybersecurity in 2021, along with some of the biggest cybersecurity threats that target the industry.
The healthcare sector has glaring cybersecurity vulnerabilities that make it an obvious target for cyberattacks. Over the last three years, a staggering 93% of healthcare organizations experienced a data breach, while 57% of healthcare organizations have had more than 5 breaches. We’ll be covering some general stats on the issue, along with cybersecurity risks, impacts, and the steps healthcare companies can take to safeguard against cybersecurity incidents.
General Stats About Healthcare Cybersecurity
We’ll start things off with a few general stats, so you can get a feel for the state of data breaches, cyberattacks, and cybersecurity in the healthcare sector.
High-Profile Incidents
There have been several high-profile cyberattacks in the healthcare industry. Although healthcare cyberattacks may not always be on the same scale as other industries (the Marriott International breach affected 500 million customers), the sensitive nature of work in the healthcare industry means cyberattacks can be much more damaging.
Given the treasure trove of personal information that can be found on the servers of hospitals and healthcare corporations, it’s unsurprising that the majority of hackers target this data with their attacks.
Patient data like names, addresses, contact details, and social security numbers can be stolen or held for ransom by hackers, while sensitive health data such as health insurance information and medical history can be used to target patients with scams and fraud.
In late December 2020, we published a report outlining a data breach in the Vietnamese medical company Innovative Solution for Healthcare (iSofH). The Safety Detectives cybersecurity team, led by Anurag Sen, found iSofH’s server in open form, exposing 80,000 people.
Healthcare data breaches can affect millions of people. One look at the top 10 healthcare data breaches of all time demonstrates the sheer size of some healthcare leaks.
|
Top 10 Healthcare Data Breaches of All Time |
|||
| Rank | Company | Date | No. of People Affected |
| 1. | Anthem Blue Cross | January 2015 | 78.8 Million |
| 2. | American Medical Collection Agency | March 2019 | 26.1 Million |
| 3. | Brazil Ministry of Health | November 2020 | 16+ Million |
| 4. | Premera Blue Cross | January 2015 | 11+ Million |
| 5. | Excellus BlueCross BlueShield | September 2015 | 10+ Million |
| 6. | UK National Health Service (NHS) | July 2011 | 8.6 Million |
| 7. | MedicareSupplement.com | May 2019 | 5 Million |
| 8. | TRICARE | September 2011 | 4.9 Million |
| 9. | University of California, Los Angeles Health | July 2015 | 4.5 Million |
| 10. | Community Health Systems | June 2014 | 4.5 Million |
The largest healthcare breach by far involves Anthem Blue Cross, an American health insurance company and the largest company in the Blue Cross Blue Shield Association.
The Anthem cyberattack affected a staggering 78.8 million people. Most of the victims affected in the breach were health plan members, though some non-members did have their personal details leaked.
The breach was caused by a phishing attack. On February 18th, an Anthem employee opened a phishing email that infected the user’s computer with malicious files. This allowed the hacker to gain access to 90 different systems within the company, escalating their privileges, and eventually reaching Anthem’s data warehouse.
An investigation carried out by the insurance commissioners’ examination team and security firm Mandiant outlines how names, social security numbers, medical ID numbers, addresses, dates of birth, emails, and employment details were all leaked during the breach.
The hacker is thought to be a “nation-state” hacker, acting on the behalf of another government.
Since the breach, Anthem has invested heavily in cybersecurity measures, spending $260 million on consultants, security improvements, better systems of notification, and credit protection for impacted individuals.
Healthcare Cyber Attack Impact
From innocent customers to staff members and healthcare corporations, cyberattacks can have a huge impact on everyone involved.
These impacts can be broken down into 3 different types:
- Financial
- Organizational
- Personal
Financial Impact
Financially, cyberattacks cost companies a huge amount of money. A survey by HIMSS found that 20% of healthcare cybersecurity professionals claim that cyberattacks result in a monetary loss, such as wire fraud or extortion. Healthcare companies may also have to pay damages to affected individuals. If a company has handled customer data carelessly, data protection legislation could also enforce a hefty fine.
Organizational Impact
Cyberattacks can have an organizational impact on healthcare companies as well. Healthcare brands are built on the image of safety and protection. By putting customers at risk, healthcare companies can suffer reputational damage — decreasing trust amongst customers. 50% of healthcare cybersecurity respondents are not confident of recovering from a cyber attack.
Cyberattacks can lead to a reduction in productivity, too. 28% of respondents in the healthcare industry said that cyber attacks disrupted IT operations, while 27% claim that attacks disrupted the operation of the business. Ransom attacks, or data leaks, could force hospitals to close or prevent the use of medical technology. This leads to financial damages for the company and potential health impacts for patients.
Personal Impact
Healthcare cyberattacks cause significant damage to people, their finances, or their physical and mental well-being. A hospital that closes its doors, or suffers a crippling reduction in productivity, may have to cancel appointments — leading to health impacts on patients.
Around 50% of healthcare data breach victims suffered medical identity theft, with an average out-of-the-pocket cost of $2,500 for patients. The stress associated with cybercrimes like identity theft, financial fraud, tax fraud, and other crimes related to a cyberattack, can have huge implications on the mental health of the victims involved.
Whose Data is Leaked?
Overwhelmingly, the data leaked in healthcare data breaches belongs to patients, rather than other business entities and staff members. Across all industries, public data containing personal information is exposed in 80% of data breaches — and the trend is no different in healthcare.
All 10 of the largest healthcare data breaches involve patient data, with more than 160 million public records exposed in the process. Just one breach from the top 10 involved business data. The AMCA’s data breach leaked lab results for one of the companies using its services, although this is thought to be just a fraction of the total number of files that were leaked.
Cyberattacks Are Damaging
From 2005 to 2019, almost 43.38% of all health data was compromised in a data breach.
In fact, hacking ranks as one of the most damaging and impactful types of data breaches for healthcare payers and providers.
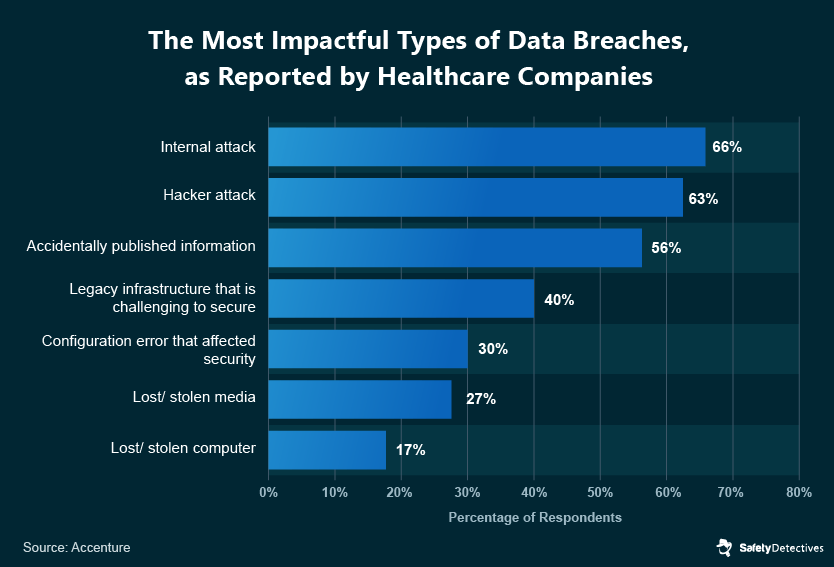
Costs
If online data breaches are so impactful, how does this impact translate into monetary damage?
With so much sensitive data at stake, healthcare data breaches are some of the most damaging leaks when compared to any other industry.
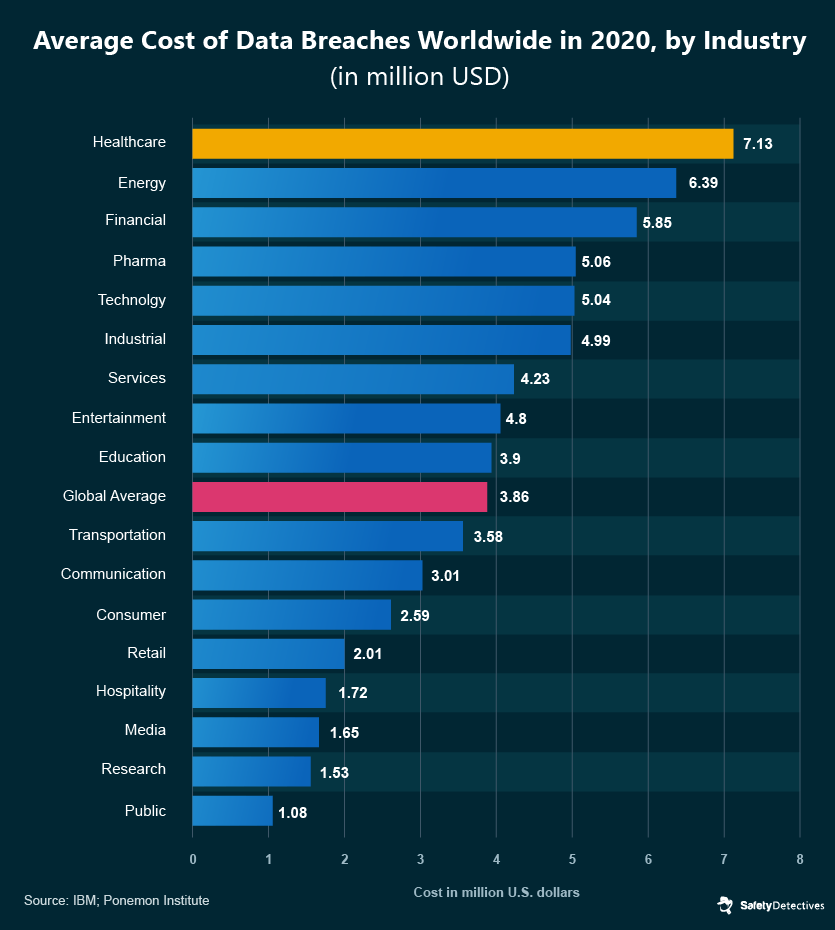
That’s right, a healthcare data breach costs a whopping $7.13 million on average when compared to other sectors. The healthcare industry is closely followed by the energy and financial sectors, at $6.39m and $5.85m cost per data breach. However, I’m sure this is a table no one wants to be leading.
The cost of healthcare breaches has risen from $6.45 million, a 10% increase between 2019 and 2020.
When compared to other industries, the latest data shows healthcare experienced the second-highest increase in cost-per-breach in 2020, just behind energy.
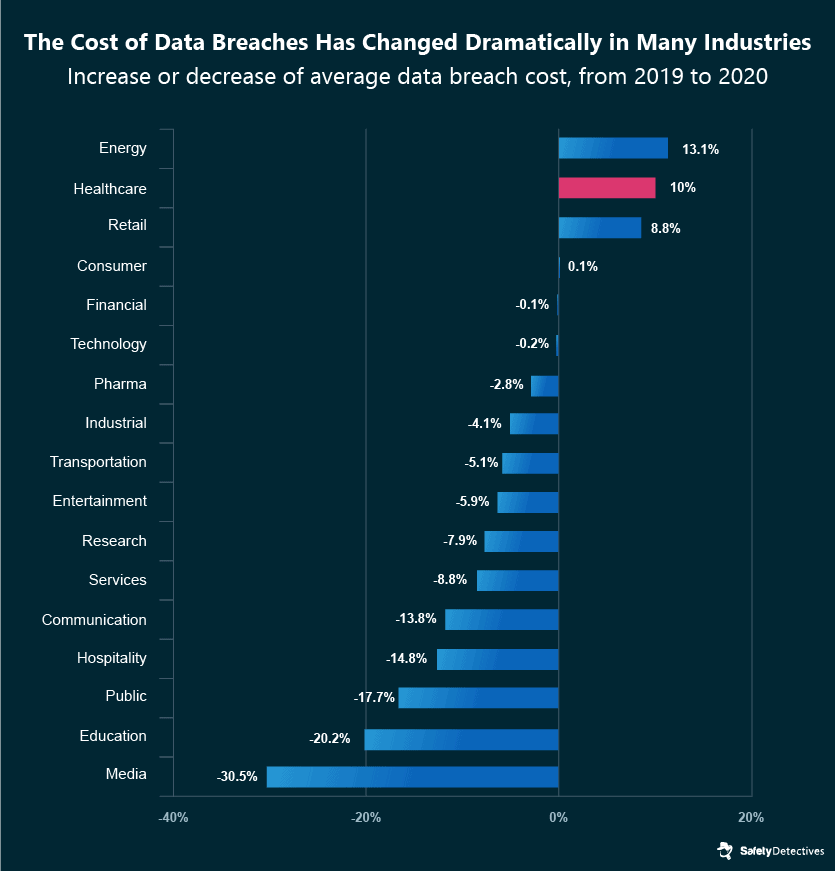
In addition to direct costs associated with a data breach, companies who have mishandled customer data could be under threat of government legislation and data protection laws. GDPR, for example, can fine companies for as much as €20 million, or 4% of the companies annual income.
Medical Data is Valuable
Once a hacker has acquired a healthcare customer’s data, this data can be sold for a large return on the dark web.
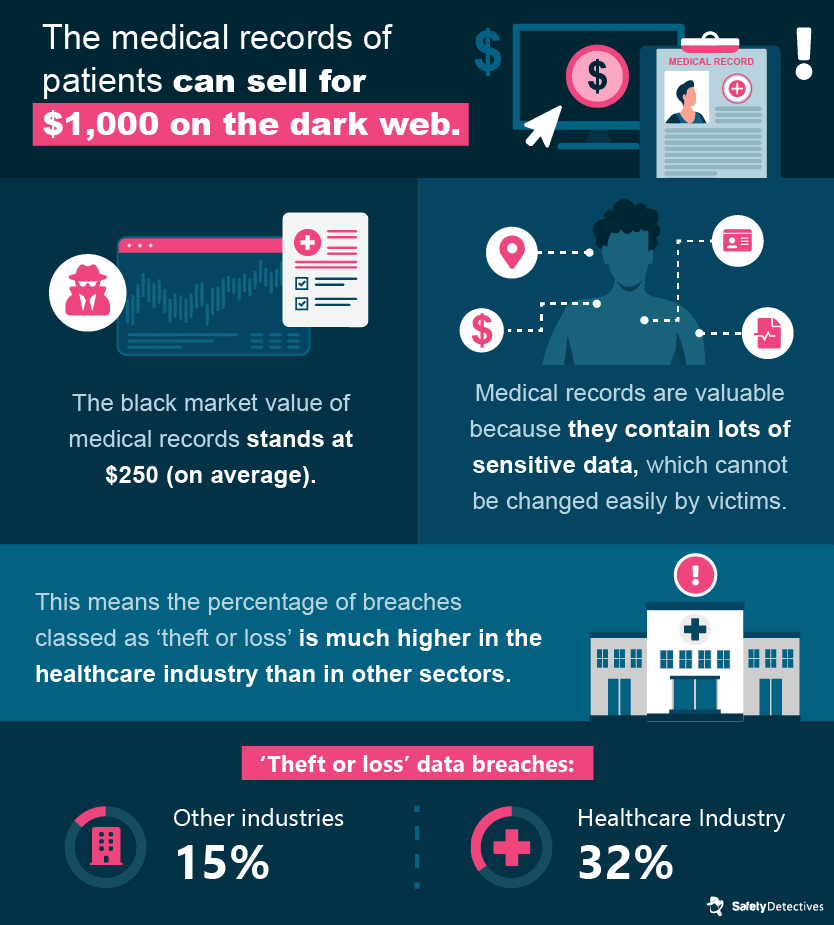
Medical records contain a bounty of unalterable personal details, like a person’s medical history, behavioral tendencies, demographics information, health insurance and social security number, contact information, and home address. While credit cards can be canceled and further crimes can be prevented, information on medical records is largely unchangeable and could lead to exposure to cybercrime for several years.
It’s for this reason that medical records are so valuable to hackers, and are targeted with such high frequency.
Cybersecurity Spend in Healthcare
Despite continued cyberattacks that are extremely damaging to healthcare companies and their customers, the healthcare industry invests an embarrassingly small amount of resources into cybersecurity, although this is expected to rise in the coming years.
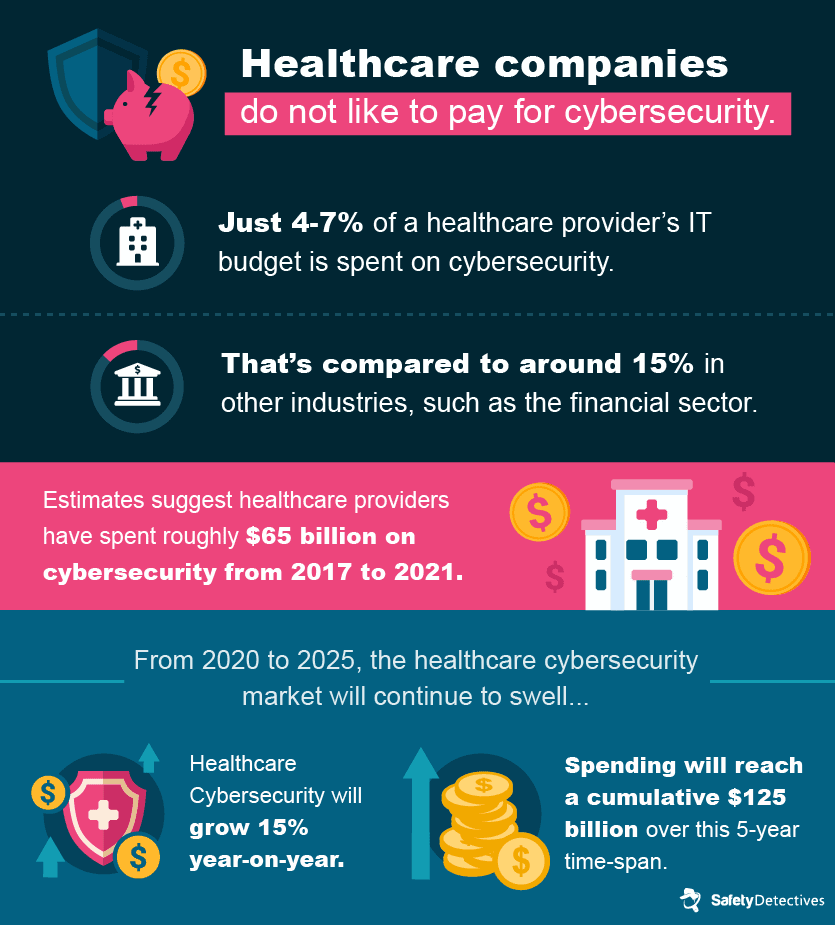
This expected growth is in part due to the expected growth of global healthcare spending — which could reach $18 trillion in 2040.
The current spend on healthcare cybersecurity (or lack thereof) is another major factor. Healthcare companies are not putting enough resources into cybersecurity. One report from SecurityScorecard ranks healthcare 9th in security rating compared to other industries. This is one of the reasons healthcare providers are being targeted with such ferocity and to such a damaging extent.
Some choose to save costs rather than protect themselves from cyberattacks, placing executives in charge of cybersecurity. One-third of healthcare executives, unqualified in cybersecurity, purchase cybersecurity tools for their business.
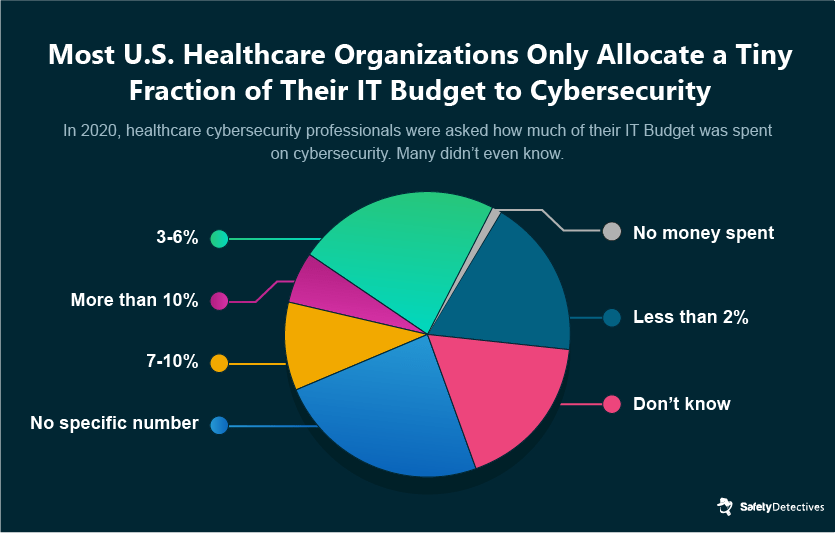
Of all healthcare organizations, just 16% claim to have fully functioning cybersecurity measures in place. A small number of healthcare firms do not spend any budget on cybersecurity at all.
Cybersecurity Rating by Nation
So, which countries are best placed to deal with cybersecurity incidents in healthcare? With healthcare one of the most targeted sectors across the world, a quick look at cybersecurity ratings should tell us which countries are most at risk. The national cybersecurity index measures a nation’s cybersecurity level, preparedness for cyberattacks, and response to cyber incidents.
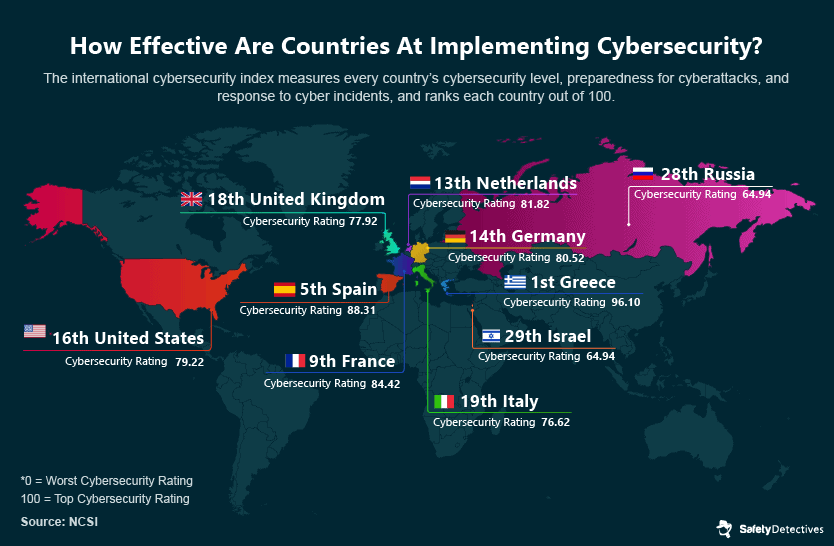
The data goes some way to explaining why certain countries suffer such crippling healthcare cyberattacks. Brazil, for example, has an awful cybersecurity system protecting the data of its 211 million-strong population. It’s no surprise then that data for 16 million Brazillian citizens was lost in a data breach on Brazil’s Ministry of Health in 2020. Brazil’s Ministry of Health also exposed the medical data for more than 220 million citizens, though it remains to be seen if the data has been leaked.
Australia is another nation that has been vulnerable to healthcare cyberattacks, with its poor national cybersecurity exposed during the COVID-19 pandemic. In Western Australia, hackers accessed and published more than 400 pages of communications between doctors and health officials regarding COVID-19 patients.
Cyberattacks Are Getting Worse
Cyber attacks and breaches in the healthcare industry are becoming increasingly severe. Healthcare cyberattacks are now more frequent, with bigger financial losses and more patient data compromised in an exposure. These factors are only on an upward trajectory.
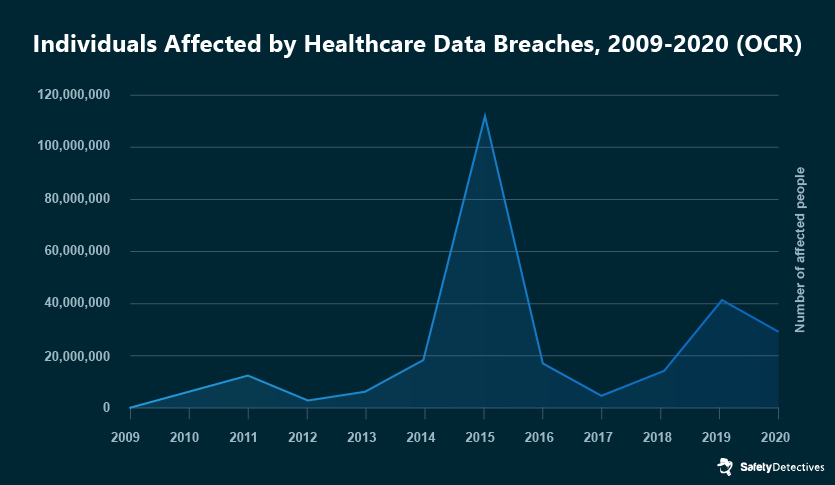
Over the previous decade (2010-2019), 81.9% of all 850 analyzed hacking/IT incidents in healthcare companies occurred in the last 4 years of the decade (2016-2019). 32.23% of these healthcare breaches were reported in 2019.
This generally upward trend can be seen in HIPAA data. Disregarding an anomalous spike in 2015 (caused by Anthem’s breach), more records are exposed in healthcare breaches now than, say, 10 years ago.
Cybersecurity threats have become a very recent (and extremely serious) concern for healthcare providers. In late 2020 and early 2021, cybersecurity threats have continued to worsen.
Not only have attackers realized the vulnerabilities in current healthcare cybersecurity systems. The increase in cyber attacks is largely down to the COVID-19 pandemic, too.
We’ll cover the specificities of the ‘Covid-effect’ later on, but essentially healthcare providers are preoccupied with the pressures of a global pandemic. Resources are being plowed into a COVID-19 response, drawing attention away from cybersecurity.
Healthcare has been targeted by a wave of cyberattacks as a result.
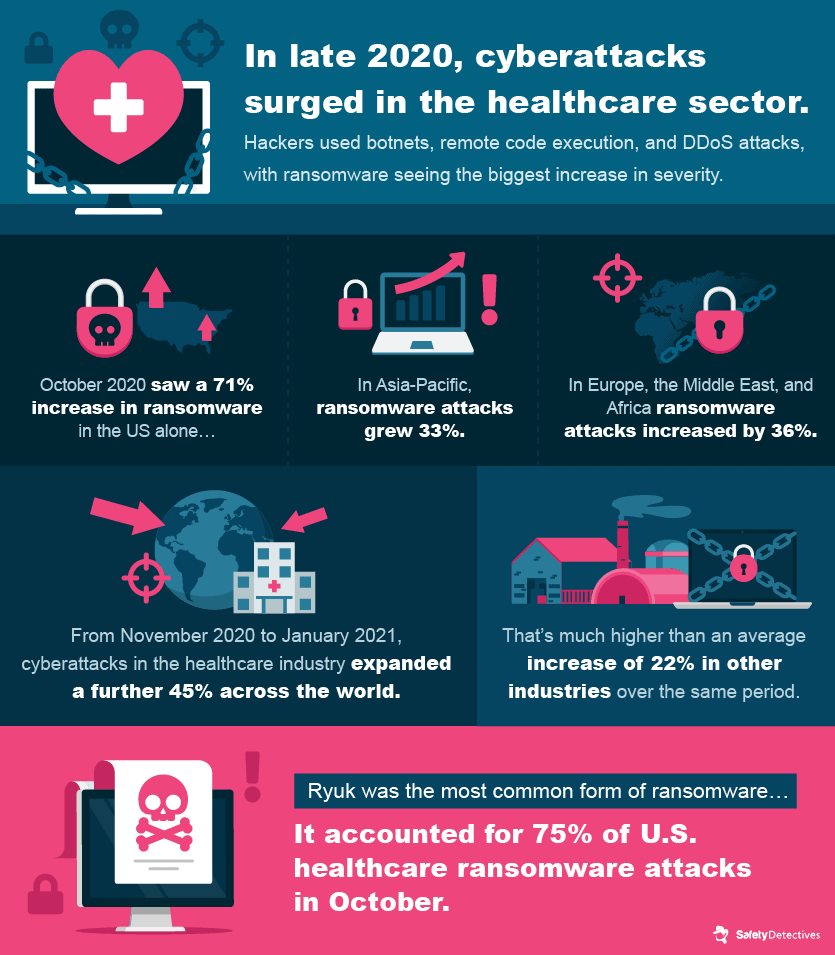
Geographically, Central Europe experienced the most volatile increase in cyberattacks against healthcare organizations, at 145%.
Canada and Germany were two of the worst-affected countries, with a 250% and 220% increase respectively.
Cybersecurity Risks in the Healthcare Industry
We’ve covered the latest trends in healthcare cybersecurity for 2021. To know the issue inside out, we must have an understanding of all the risks that healthcare providers are facing.
How Much is Healthcare Targeted?
The healthcare industry continues to be the most targeted sector for cyberattacks. In 2020, 79% of all reported data breaches were in the healthcare sector.
Over the previous 15 year period, data breaches in the healthcare sector have accounted for roughly 62% of all breaches, and this figure rose as high as 77% in 2019.
| Data Breaches by Sector 2005-2019 (based on PRC database) | ||||
| Sector* | Data Breaches (2005-2019) | Data Breaches (2015-2019) | ||
| Number of Breaches | Percentage (%) | Number of Breaches | Percentage (%) | |
| EDU | 671 | 10.55 | 64 | 3.08 |
| BSF | 410 | 6.45 | 194 | 9.36 |
| BSO | 426 | 6.70 | 113 | 5.45 |
| MED | 3912 | 61.55 | 1587 | 76.59 |
| GOV | 561 | 8.82 | 45 | 2.17 |
| NGO | 75 | 1.18 | 7 | 0.33 |
| BSR | 300 | 4.72 | 62 | 2.99 |
| Total | 6355 | 99.97 | 2075 | 99.97 |
*EDU: Educational Organizations; BSF: Business-Financial; BSO: Business-Other; BSR: Business-Retail (Includes Online Retail); Med: Healthcare Service Providers; GOV: Government and Defense Institutes; NGO: Non-Government Organizations.
Highest Risks
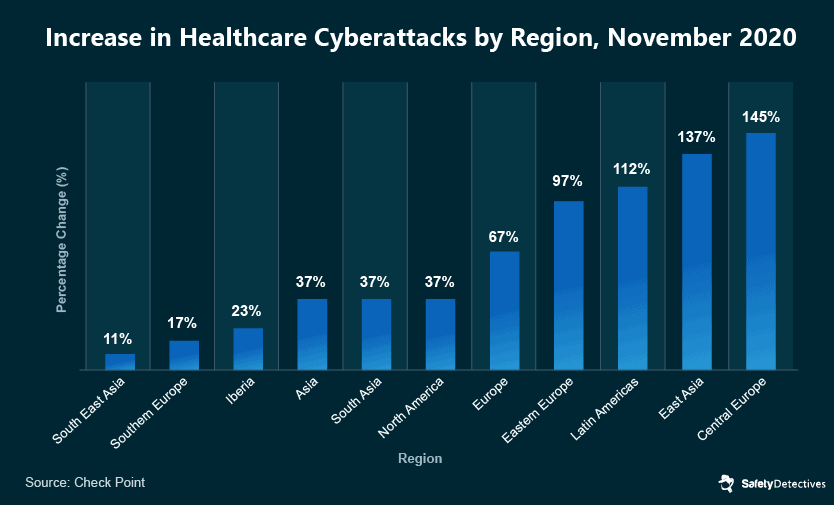
In 2020, hacking and IT incidents were responsible for 69% of all healthcare breaches in the United States.
Hackers looking to steal data or carry out ransomware, DDoS, or any other type of cyber attack, will exploit certain vulnerabilities to gain access to a hospital’s systems and carry out malicious crimes.
Wandera, a company that provides businesses with cloud security solutions, published its findings from months of research in late 2020. Wandera’s report evaluated data on tens of thousands of users in a vast global database of healthcare organizations. The report’s findings demonstrate the different ways in which hackers are launching their attacks, by the percentage of organizations affected.
|
High-Risk Entry Points for Hackers in the Healthcare Industry |
|
| Threats | Healthcare Organizations Affected |
| Malicious network traffic | 72% |
| Phishing | 56% |
| Vulnerable OS (high risk) | 48% |
| Man-in-the-middle attack | 16% |
| Malware | 8% |
Wandera’s research outlines two different types of man-in-the-middle attacks as particularly troublesome.
- SSL stripping – Where an intermediate server disguises itself as a legitimate service.
- Targeted certificate spoof – Where an intermediate server actually poses as a genuine service.
A survey from HIMSS ranks the prevalence of ransomware and malware as high as 20%, and while we await data for late 2020/early 2021, the recent spike in ransomware attacks across the sector means this value could now be even higher.
What Are Each of These Risks?
- Malicious network traffic refers to any attack that begins with network access from an app or web service. This traffic can carry out malicious behavior, such as downloading unauthorized software onto a healthcare computer or device. From here, hackers can gather information or disrupt the function of hospitals/devices.
- Phishing refers to any attempt to deceive users by convincing them to click a link, follow a web form, or submit sensitive personal data. If a user bites on a phishing attempt, hackers could gain access to a hospital’s system.
- Hackers could also target any Vulnerable OS (operating system) that is used within a healthcare organization. Older devices, or devices using older software, are not as secure against the threat of hackers when compared to newer devices. Some medical devices are also not designed with cybersecurity in mind.
- Man-in-the-middle attacks occur when a device has been manipulated to completely trust an unauthorized third party (i.e. a hacker). From here, a cyberattacker can transition through hospital systems, and gain access to information.
- Malware is an application or software that is created to cause harm or gain unauthorized access to a mobile device or system.
Prevalence of Specific Threat Vectors
Specific threats, like ransomware, distributed denial-of-service attacks, and insider threats, make up a significant portion of all cyber attacks.
For data breaches alone, Tenable researchers found that ransomware was the primary threat in almost half of all data-related attacks.
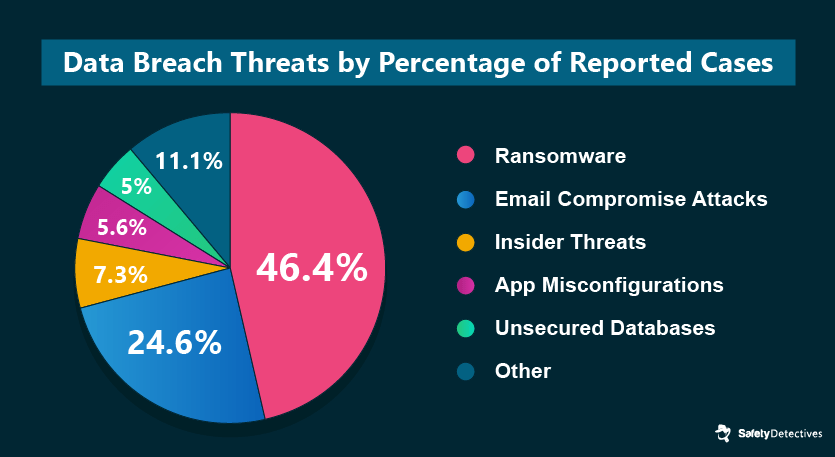
Ransomware is a form of malware that holds stolen data behind a paywall, with the threat of publication should an organization choose not to pay the ransom. Around 23% of healthcare organizations pay a ransom to retrieve stolen data.
Cyberattackers using ransomware gain access to healthcare servers primarily through exploiting two different vulnerabilities in Virtual Private Networks (VPNs): the CVE-2019-19781 vulnerability and the CVE-2019-11510 vulnerability.
Elsewhere, hackers can also capture hospital systems with the use of DDoS attacks. “Distributed denial-of-service” attacks target weak operating systems or old devices. They attempt to render a device or network resource unusable by taking control of it and disrupting the host device’s services.
DDoS attacks can result in the operations of a hospital shutting down, and hackers can hold hospitals to ransom before returning networks to working order. There were 10 million DDoS attacks across the world in 2020, with healthcare institutions seeing a sharp increase in cases. In Asia and the Pacific, DDoS attacks on healthcare organizations grew by 98% in the first half of 2020.
Common Cybercrimes
Criminals can carry out all manner of fraudulent and criminal activities with sensitive personal data.
One of the most common crimes victims can experience is long-term identity theft and fraud. Over 70% of healthcare data breaches involve sensitive demographic or financial information that can be used to conduct crimes to this effect. By adopting the victim’s identity, criminals can open credit card accounts and loans in the victim’s name and take the money for themselves. Tax fraud and home equity fraud are two more avenues criminals may choose to take.
Criminals can also leverage details about a patient’s disease or terminal illness to conduct scams specific to their condition. This could include selling a miracle “at-home cure” to these poor individuals, which is particularly cruel.
There is the issue of medical identity theft and fraud, too. With medical records, a criminal could obtain prescription medications, file fraudulent medical and insurance claims, and access certain medical services for free. It is estimated that, in the U.S. alone, medical fraud can cost anywhere from $80 billion to $230 billion every year.
Medical devices are also at the mercy of criminals. If hackers are not holding healthcare institutions to ransom over customer data, they are taking control of medical devices, disabling them, and demanding payment before devices can be restored to working order. Healthcare providers must pay the ransom or risk patients dying without adequate healthcare support.
Medical devices are not designed to deal with the modern threat of hackers. Criminals can also use medical devices to gain access to other servers, where they can get to sensitive personal data.
IoT devices are vulnerable to cyberattacks. We talk about these in-depth further down the page.
High profile ransomware attacks on medical devices and systems include:
- WannaCry – which affected institutions in 150 countries, and brought the UK’s NHS to a standstill. The NHS even had to deny patients A&E assistance.
- SamSam ransomware – which held hospital records in the US behind a paywall. One hospital paid $55,000 to retrieve the data.
- Orangeworm – targeted several different health institutions across the world, accessing equipment and systems — in all likelihood to conduct espionage.
Popular Scams
Once a hacker or criminal has acquired a patient’s contact details, a few different scams are common within the healthcare industry.
One way in which scammers will attempt to con victims is through the offer of health and medical products. They could target victims based on their medical history. Generally, medical product scams are split into two categories: fake online pharmacies and miracle cures.
In a fake online pharmacy scam, the criminal will trick victims into paying for medical products. Of course, the offer is not from a legitimate pharmaceutical company. Customers will either receive bogus medications that do not work or nothing at all.
These scammers may even have a website that looks the part, and cheap prices without the need for a prescription that will seem too good to be true — because they are!
Miracle cure scams will offer quick, easy, and effective medications that provide hope to people with serious or chronic health conditions. These scams prey on vulnerable people in desperate situations. Miracle cure scams could offer treatments for anything from AIDS, cancer, or dementia, to arthritis or the common cold. Scammers may also claim that their product cures all ailments, which is not possible. Scammers can charge huge sums for these specialized treatments, only for victims to find out they are not legitimate.
Risk Data in Healthcare
As we have already established, the kind of data stored in hospitals is risky. That’s why it’s so valuable to cybercriminals.
An extensive list of sensitive personal data is stored on medical records, from patient phone numbers to unalterable details, like a social security number.
But there are big risks involved for the healthcare institutions, too. Breaches can cripple the operations of a healthcare institution. 61% of healthcare cybersecurity respondents said that cybersecurity incidents disrupted non-emergency clinical care, while 28% believe emergency services were negatively affected. 17% of respondents believe a breach led to serious patient harm. Of course, there can be legal implications wherever medical negligence is a concern.
Financial records, data on business operations, and valuable research into treatments or new technologies may also be stored on a healthcare organization’s database. Through accessing these files, hackers can conduct “business espionage,” gathering data on the business operations of a company. Cancer treatments in China have undercut the US market in recent years, and many people attribute this to the abundance of Chinese nation-state hackers involved in big data breaches.
One Frost Radar report highlights how hacks on financial records and revenue management systems can rack up heavy costs for healthcare organizations — with low insurance compensation and a reduced patient footprint.
Risk of IoT in Healthcare
IoT (or “Internet of Things”) is a new technology that allows hospitals to monitor a patient’s care and health data in real-time. The technology is potentially groundbreaking, as it can help healthcare organizations provide a better quality of service for patients.
Doctors have the data at their fingertips to know exactly why treatment is not working. For example, if a patient with a memory issue is not taking their tablets, tablets with an edible tracking chip inserted could let the doctor know.
IoT’s effectiveness has led to its widespread use throughout healthcare organizations. 60% of healthcare providers across the planet have incorporated IoT into their facilities, with the medical IoT market set to reach $136.8 billion worldwide in 2021.
However, opportunistic cybercriminals are now beginning to realize that IoT devices are particularly vulnerable. These devices are connected to the internet, and they provide a link to medical records and sensitive data. What’s more, IoT devices are relatively unprotected against hackers, all of which combine to make IoT a worthwhile target for cyberattacks.
If an IoT device uploads its data to a cloud-based database, something as simple as a poorly configured security patch could be the cue for hackers to conduct their attacks. Using the IoT device as an entry point, they could access the database and expose all of the files.
According to Palo Alto Networks, internet-connected medical imaging machines — such as MRI — are especially susceptible to these attacks. In 2020, 83% of medical imaging devices were vulnerable to hackers, a figure that has increased significantly since 2018 (56%).
In a survey conducted with Fortune 1000 medical device companies in the US, just 18% believed their medical device security was strong. Elsewhere, research suggests cyberattacks involving IoT could make up for 25% of all healthcare cybersecurity incidents.
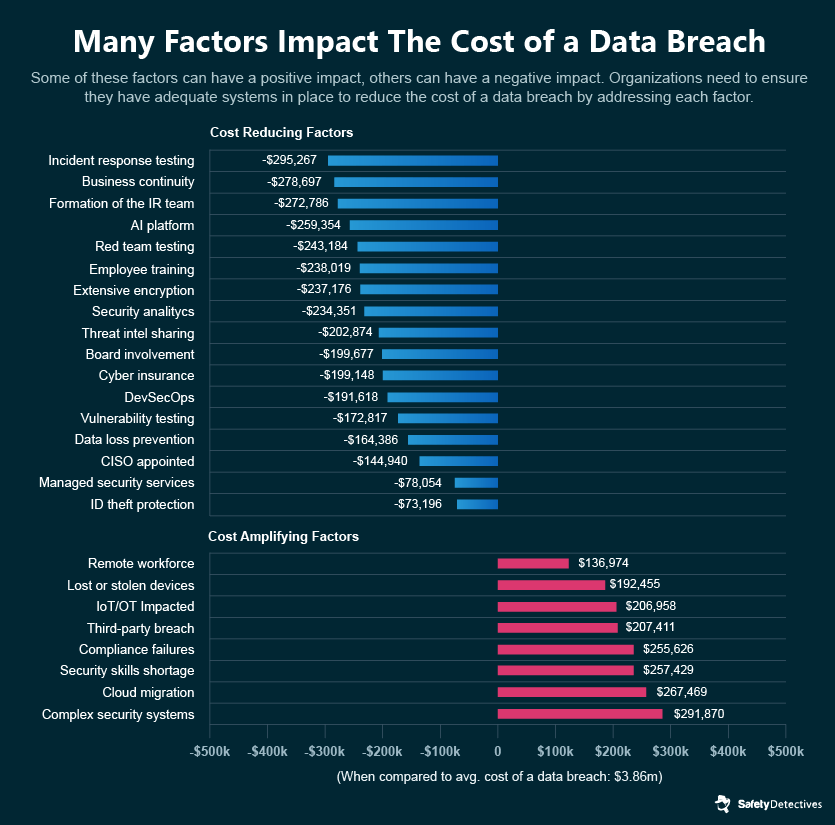
Overall, IoT has a negative impact on the total cost of a data breach.
The Covid Effect
The COVID-19 pandemic has introduced fresh challenges for everyone. In the healthcare sector, however, it has presented issues in more ways than one.
The pandemic has seen a huge spike in cybercriminal activity. In 2020, cyberattacks almost doubled compared to 2019, rising from 2,103 reported breaches to 3,950. In the United Kingdom, the first month of lockdown (March 2020) saw a 400% increase in scams.
Healthcare institutions have been hit harder than most by the rise in cybercrime. Verizon reported that confirmed data breaches in healthcare rose by 58% in 2020.
The Pandemic is Causing More Hacks
The pandemic has facilitated a rise in cybercrime in 2020, but why is that the case?
In the healthcare industry, the pandemic has stretched the resources of hospitals, clinics, vaccine developers, and medical manufacturers to breaking point. Healthcare organizations have been understandably focused on the tough task of containing COVID-19 and treating patients. In doing so, attention has slipped away from maintaining a good level of cybersecurity. Like vultures, cybercriminals have lept on this opportunity to take full advantage.
The critical nature of medical data, especially during a pandemic, has also made healthcare institutions a popular target. Hospitals or vaccine research facilities struggling with the pandemic are reliant on data getting from A to B quickly. Cyberattacks disrupt or even take control of this data, and desperate healthcare companies will pay whatever it takes to retrieve their data as soon as possible.
Emerging Cyber Crimes During COVID-19
Some common cyber crimes have emerged during the pandemic.
COVID-19 Phishing Scams
Phishing scams related to COVID-19 have been one recent phenomenon. Email phishing attacks have been the most common cause of data breaches across all industries while people are working from home. In healthcare, phishing emails have capitalized on desperation and urgency, with subject lines referencing test results or PPE to draw healthcare workers into clicking a link. Some scams have promised at-home cures for COVID-19, targeting the fear and uncertainty caused by a health crisis. In April 2020, Google blocked 18 million malware and phishing emails related to COVID-19 every single day.
Big Health Data Breaches
Criminals have also targeted big health corporations with data breaches due to their public presence, and abundance of valuable data. One example would be the increase in attacks on the World Health Organization. During the pandemic, cyberattacks on the WHO more than doubled — and some of these have been successful. In April 2020, 450 active WHO email addresses were leaked along with thousands of COVID-19 response team emails.
In vaccine research labs, another form of critical data is targeted by hackers. The public attention on COVID-19 vaccines has made acquiring research data a fruitful venture, and there have even been reports of nation-state hackers looking to steal information for their country’s vaccination campaigns.
Tracked Logins
Working from home does not just allow hackers to carry out more phishing scams. There are other ways hackers are stealing data and accessing sensitive information. Companies utilizing Zoom and other video-conferencing programs have had their streams hacked or login details tracked. Hackers can listen in on meetings and gain insights into a company’s business.
Employees logging on to a company website or employee portal have also been tracked by hackers. While big drug companies have procedures in place to deal with this kind of threat, smaller institutions (such as universities) that have been involved in vaccine research are not awake to login tracking and have been hacked as a result. One technique hackers use is “password spraying,” where they pepper accounts with generic passwords until they eventually gain access.
COVID-19 Apps
COVID-19 apps, such as track-and-trace or venue check-in apps, have been particularly exposed to hackers. These apps have been produced quickly and, in some cases, not to a very high standard. COVID-19 apps contain a lot of sensitive patient data, and sometimes their security leaves a lot to be desired. GDPR even publicly criticized the UK for lackluster data protection in its test-and-trace project.
There have already been high-profile breaches linked to these apps across the world. Interlust research found shocking vulnerabilities in COVID-19 track-and-trace apps, with 85% of them leaking data. Healthcare and medical apps in general are open to cyberattacks, too. 71% of these apps contain at least one major vulnerability, leaving them open to a data breach.
Healthcare apps are painfully easy to hack. In fact, 91% of apps failed a cryptographic test. Once inside, hackers can steal data, take control of linked devices, or breach systems.
COVID-19 apps lack simple protection technologies like code obfuscation, tampering detection, or white-box cryptography. These technologies are required to mitigate the risk of a cyberattack. 83% of serious cybersecurity threats to COVID-19 apps could be blocked by better protection technologies.
The Impact of “Working From Home”
As we’ve mentioned above, working from home has introduced new opportunities to hackers, whether that is through targeted phishing scams or hacking employee login credentials. Research conducted by IBM highlights how “WFH” has changed the impact of cybersecurity incidents.
On average, the cost of a data breach has increased significantly because of WFH — by $137,000 per data breach according to IBM.
So why are data breaches more frequent, and at a higher cost, when people work from home?
Teams are not as interconnected if they’re working in different locations, and individuals are more likely to fall for phishing scams when they are left to their own devices. Employees are not as likely to air concerns about potential scams and could lose focus and click on a link without thinking. 47% of employees working from home cited distraction as the reason they fell for a phishing scam.
Cybersecurity teams are not as efficient working from home, either. This leads to big delays, as teams attempt to contain cybersecurity threats. 76% of remote workers believe WFH has increased the time it takes to respond to cyberattacks and breaches.
High Profile COVID-19 Data Leaks
There have been high-profile incidents across the planet that have leaked COVID-19 data.
Pfizer Breach
One publicized incident involved the pharmaceutical company Pfizer. Pfizer has been a leader in COVID-19 vaccine research, with its vaccine candidate recently becoming available. In December 2020, hackers targeted Pfizer with cyberattacks and on December 9th, 2020, the European Medicines Agency (EMA) announced that hackers had stolen data on the vaccine candidate, which was released online shortly after the breach.
The files that were taken related to the regulatory submission of Pfizer’s vaccine to the EMA, which was stolen from an EMA server. A small number of word documents, PDFs, email screenshots, PowerPoint presentations, and EMA peer reviews were exposed in the breach — though ultimately the leak was not significantly damaging to Pfizer.
Wales Patient Data Breach
In Wales, COVID-19 patient data for 18,000 Welsh residents was leaked when an employee working for Public Health Wales accidentally posted data on a public-facing database, rather than a secure internal server.
The initials, dates of birth, geographical residences, and gender details of COVID-19 positive patients were left on an unsecured server for 20 hours before being taken down in late August 2020. For 16,179 people, the risk posed by the breach was relatively low. However, 1,926 people living in nursing homes or other enclosed settings could have been identified by the available information.
Brazil COVID-19 Data Breach
The personal details and health information of 16 million Brazillian citizens became exposed when a hospital employee uploaded a spreadsheet onto GitHub software. The spreadsheet contained government usernames, passwords, and access keys that provide entry onto systems containing sensitive COVID-19 patient data.
Among the systems compromised were E-SUS-VE and Sivep-Gripe, the former was being used to track mild COVID-19 cases, while the latter showed data for hospitalized patients. Patient addresses, IDs, and healthcare records containing medical histories and medication plans were all included on these systems.
One GitHub user spotted the information sitting on the personal account of a hospital employee from Albert Einstein Hospital in Sao Paolo, and the information was removed shortly after. Information on patients from all 27 Brazillian states was exposed, including data on Brazil president Jair Bolsonaro.
Germany’s COVID-19 Tracking App
A vulnerability was discovered in Germany’s COVID-19 track-and-trace app back in June 2020. The app’s launch was met with immediate uproar, as programmers discovered a remote code execution (RCE) vulnerability in the construction of the Corona-Warn-App (CWA). The bug was found in a part of the app that validates user-supplied information, though it is thought the exposure was closed before any significant loss of data.
While there were no damages from the incident, a vulnerability in RCE could allow hackers to launch malware attacks on a massive scale. If the breach was not identified so soon, the impact could have been catastrophic.
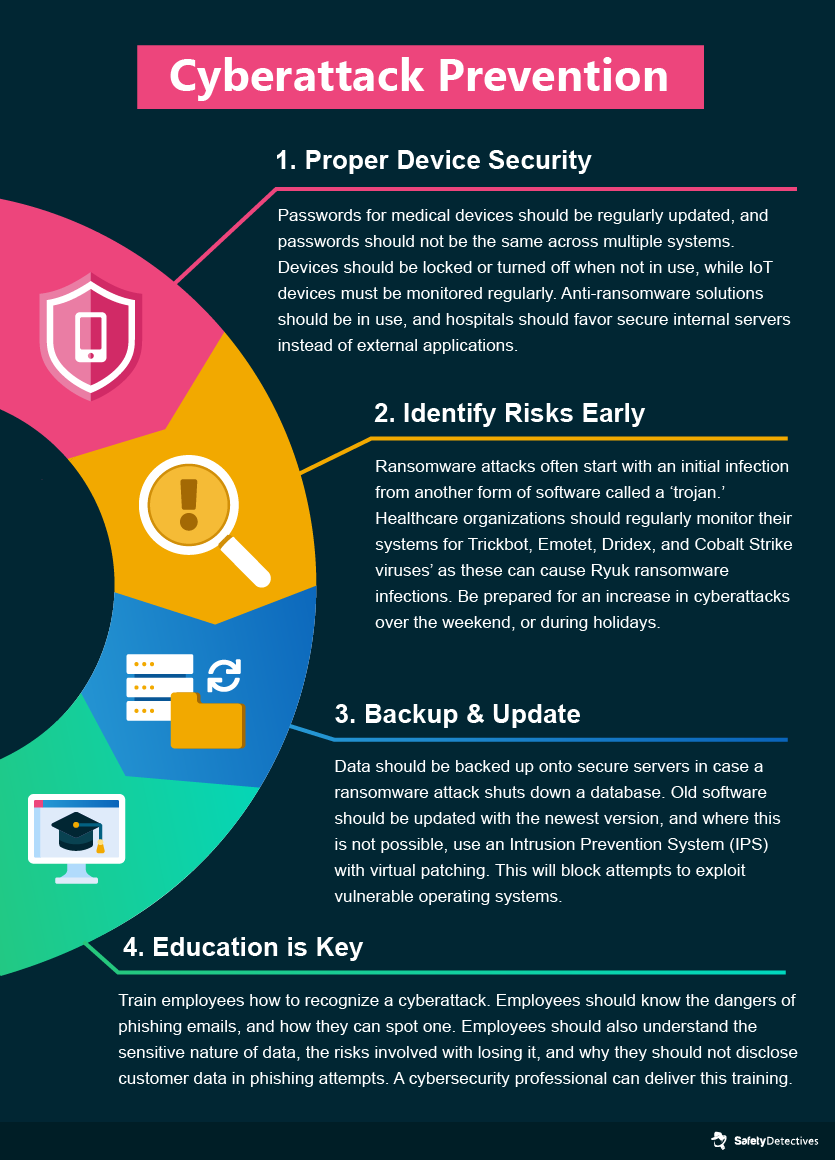
Tips to Prevent Ransomware and Phishing Attacks
Improving cybersecurity should be the number one priority for healthcare providers. Increasing the cybersecurity measures already in place leads to a reduction in the frequency of successful cyberattacks, along with a reduction in damages, both in terms of cost and the amount of data that is leaked. Organizations that fully deploy security automation save on average $3.58 million compared to companies that do not.
So, how do healthcare providers improve their cybersecurity?
Here are 4 key tips to safeguard from cyberattacks.
Final Thoughts
So there you have it, an extensive list of healthcare cybersecurity statistics covering everything you need to know on the topic. Remember to stay vigilant and do whatever you can to store data securely. You never know when a hacker may attempt to steal it!
Published on: May 20, 2021
Source of Article



