Are you certain your users are working with strong passwords on your Linux servers? Let John the Ripper show you who is and who isn’t.

Getty Images/iStockphoto
The security of your Linux servers is only as strong as the passwords used by your end users. If your users have weak passwords, it’s only a matter of time before any given ne’er do well breaks into your system to wreak havoc on your network or steal precious data.
You don’t want that.
So what do you do? You can certainly set password policies, but even then, you might have a user that predates the policy or maybe you’ve set a policy that borders on weak.
To make sure your users aren’t working with weak passwords, you can employ a tool called John the Ripper (JTR) to make sure those passwords aren’t easily crackable.
Let me show you how this is done.
Note: I demonstrate the use of this tool as a means to test your user’s passwords on your internal Linux servers. The use of this tool outside of that intent could have legal ramifications. Please use John the Ripper wisely.
SEE: 10 things companies are keeping in their own data centers (TechRepublic download)
What you’ll need
John the Ripper can be installed on nearly any Linux distribution (from standard repositories). I’ll be demonstrating on Ubuntu Server 20.04, but you shouldn’t have any problem installing the software on your distribution of choice.
How to install John the Ripper
The first thing we must do is install JTR. To do this, log in to your Linux server and issue the command:
sudo apt-get install john -y
You will also want to install a wordlist. For example, to install the large American wordlist, you would issue the command:
sudo apt-get install wamerican-large -y
To get a complete listing of the installable wordlists, issue the command:
sudo apt-get install wordlist
Go back and install any of the wordlists you want to use.
How to detect weak passwords
In order to run John the Ripper against user passwords, we need to merge the shadow and passwd files with the command:
sudo /usr/sbin/unshadow /etc/passwd /etc/shadow > /tmp/crack.password.db
We can now run john on that new file with the command:
john /tmp/crack.pasword.db
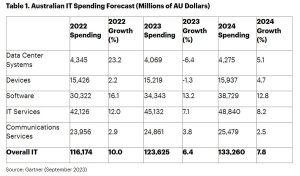
This command will take some serious time–especially if you have a lot of users for john to go through. As john runs, you can hit any key to check the status and even view revealed passwords as it works (Figure A).
Figure A
” data-credit rel=”noopener noreferrer nofollow”>

John has cracked Olivia’s password.
I created a new user (Olivia) with the password 12345. It took john less than 15 seconds to crack that password. Olivia needs to change her password immediately.
As the john command runs, you should make sure no one has access to the terminal window. You’ll probably want to do some other admin work, as you never know how long this will take. When john finishes, it will dump the results into a log which can be viewed with the command:
john --show /tmp/crack.password.db
The results of the –show command will list the users with their passwords unsalted like so:
olivia:12345:1001:1001:Olivia Nightingale,,,:/home/olivia:/bin/bash
In the above example, the cracked password is 12345.
And that’s all there is to checking to see if your users are working with weak passwords on your Linux servers. Use this tool responsibly and it can help ensure your Linux servers are safe from hackers. Use this tool irresponsibly and it can land you in a world of trouble.
Also see
Source of Article