Industrial Control Systems (ICS), which power critical infrastructure like power grids, water treatment plants, and transportation networks, are at risk in Nigeria, as a wave of malware attacks spread across Africa, according to a new cybersecurity report by Kaspersky.
A recent report by cybersecurity firm, Kaspersky, has revealed that Nigeria accounts for 28% of malicious objects targeting ICS systems in Q1 2024, an increase from 25.3% in Q1 2023.
“In South Africa the figures are 23.5% in Q1 2023 and 25.5% in Q1 2024, Kenya – 28.1% and 30.5%, while in Nigeria – the figures grew from 25.3% to 28%.”
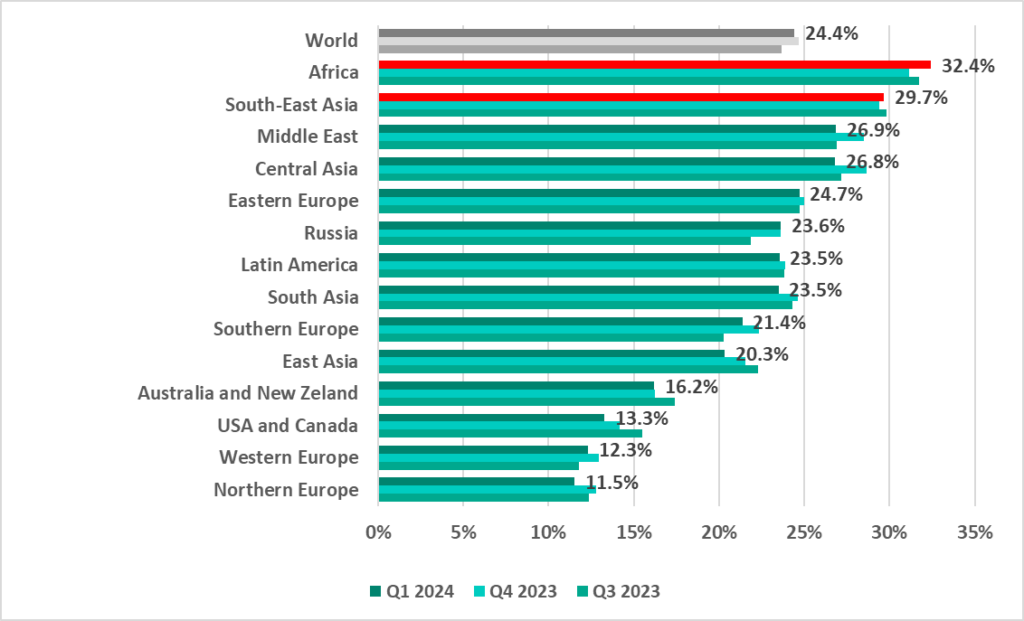
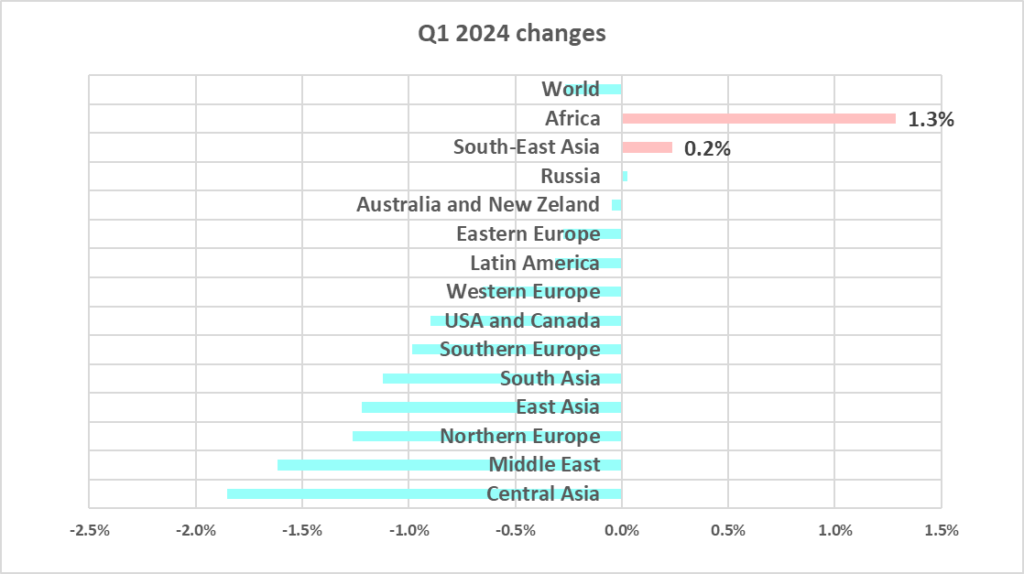
The Kaspersky report also revealed that despite a slight global decrease in blocked malware on ICS computers in Q1 2024, Africa continues to be a prime target. The global infection rate for ICS computers dipped to 24.4% in the first quarter, however, 32.4% of ICS computers in Africa faced cyberattacks during the same period.
Evgeny Goncharov, Head of Kaspersky’s ICS Cyber Emergency Response Team, emphasises the urgency of addressing this security gap. “Africa is actively integrating technologies, but it’s important to keep cybersecurity in mind and apply it to both new technologies and currently used solutions.”
Goncharov explained thus: “By a security mindset we mean implementing reliable solutions, setting up security policies and educating employees depending on their level of relation with OT. This applies to all infrastructures, but is especially important in operational technology, where risks of material consequences are very high and impact on safety is possible. We hope organisations in Africa will set the stage in the region for a future where technology and security go hand in hand.” he concluded.
ICS: Africa’s ‘facing higher prevalence of malware spread’
Unlike other regions, Africa shows a higher prevalence of malware spread via removable devices (5.6% compared to the global figure of 1.13%). According to Kaspersky, the most common initial infection methods involve tricking users into interacting with malicious online resources. These include dangerous internet resources flagged by security solutions (8.78% of blocked threats in Africa), phishing emails containing malicious scripts (6.9%), and infected documents (1.83%).
“In the first quarter of 2024, Kaspersky’s protection solutions blocked malware from 10,865 different malware families of various categories on industrial automation systems. The African region is over-exposed to threats spreading via the Internet, which are the most common initial-access tools for cyber attackers,” according to the tech security company.
Once attackers gain a foothold, they deploy a range of malware. Spyware (Trojan-Spy malware, backdoors, and keyloggers) designed to steal confidential data is a major concern, with a 6.65% detection rate in Africa. Stolen industrial secrets or operational data could be used for sabotage or sold on the black market.
Africa also experiences a higher prevalence of self-propagating malware like viruses and worms compared to other regions, according to Kaspersky. Cryptocurrency mining malware, though decreasing globally, remains a concern, these programs steal computing power from ICS systems in the form of executable files for Windows and web miners to generate cryptocurrency for attackers, potentially impacting critical operations.
“Since AutoCAD software is widely used in ICS organisations, cybercriminals also try to make use of this and similar programs creating special malware, detection of which increased in the first quarter of 2024 compared to previous quarters.”
“The Middle East and Africa lead among regions where ransomware is spread; though not high in numbers (0.28% and 0.27% of ICS computers faced these respectively), this may pose serious risk to organisations, especially if data encryption scenario is selected by cybercriminals.”
To mitigate this, Kaspersky experts recommend several steps for African organisations to improve their ICS security posture. These include implementing security solutions specifically designed for ICS systems, regularly updating software and applying security patches, conducting security audits to identify and address vulnerabilities, providing ICS security training for IT and OT personnel, monitoring ICS network traffic to detect suspicious activity, and utilising threat intelligence services to stay informed about the latest cyber threats.
Source of Article